More than network access control
ARP-GUARD as a ZTNA solution
Zero Trust is used to prevent malicious access to resources within the corporate environment and is an important tool for preventing cyberattacks. The network-based Zero Trust approach of our solution fundamentally distrusts all assets within the network and requires unique authentication for every network connection.
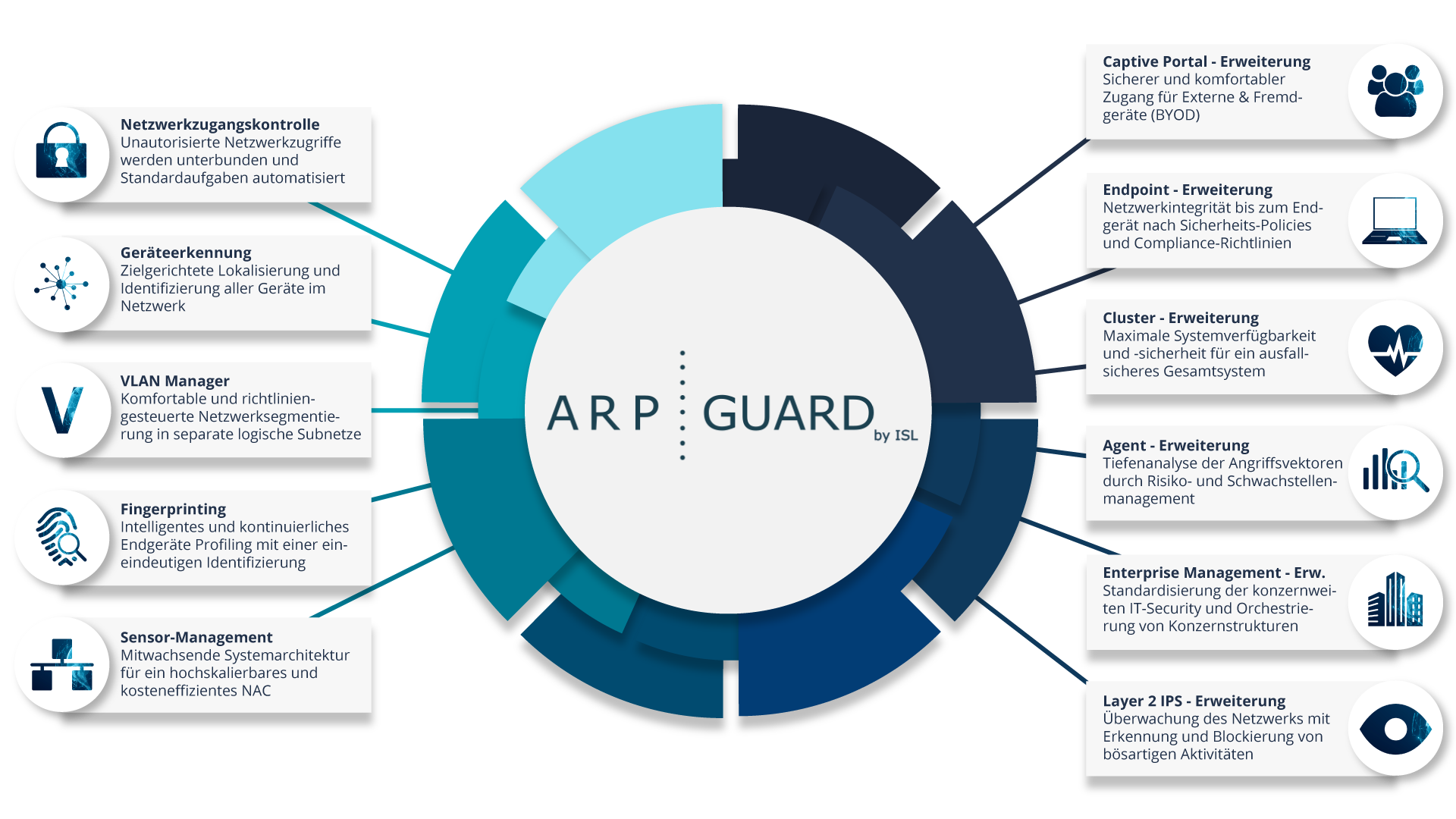
ARP-GUARD's proprietary fingerprint technology provides unique identity verification of all devices. With ARP-GUARD Network Access Control, only authorized and uniquely identified devices are granted access to the network. ARP-GUARD records every single access attempt in real time, the position of the resource and the time of each network access. Network anomalies can be detected, reported and assessed in real time with our intelligent vulnerability and risk management.
The ARP-GUARD NAC ensures maximum transparency and control for the highest IT security standards in your network. The orchestration of the entire network environment takes place at a central location and enables the definition of specific sets of rules for distributed locations. Segmentation into separate VLAN areas provides protection for sensitive areas. Devices are assigned dynamically and according to a set of rules.
In conjunction with our Enterprise Management, the scalable sensor management system architecture offers cross-location and geo-redundant protection for your company, regardless of its size.
Our ARP-GUARD is vendor- and technology-independent, giving you the freedom to choose which network technology and authentication methods you want to use. Our multivendor strategy actively supports you in standardizing your IT security within your existing IT infrastructures.
Find out more about our Network Access Control and the modular extensions.


The main advantages at a glance
- Full range of authentication methods enables mixed operation of SNMP, MAC-based RADIUS and 802.1X with the same feature set.
- Hybrid use of MAC and 802.1X authentication achieves full NAC coverage; subsequent migration from SNMP to 802.1X is easy to implement if required.
- One of the fastest implementations on the market in only 4 steps (device identification and localization / endpoint classification / ruleset definition / ruleset activation), with optional hardened physical and/or virtual appliance.
- Our solution is independent of technology and manufacturer. This allows you to homogenize your network from end-to-end as far as network security and management factors are concerned without the need for additional investment in your existing infrastructure.
- Orchestrate any number of sites and endpoints with our enterprise management using the revolutionary and highly scalable sensor management architecture.
- Intelligent real-time vulnerability and risk management using the industry standard Common Vulnerability Scoring System(CVSS), taking into account the real threat environment.
- Our solution supports you especially in the area of critical infrastructures with important certifications such as ISO 27001, ISO 27799, DIN EN 80001-1, IT Baseline Protection and the B3S standards.
- We and our partners are at your disposal with German and English-speaking support.

Would you like to become a sales partner?